
The Ultimate Solution to Protect Infrastructure Networks
OT Network Controller™ (powered by Veracity Industrial Networks), the revolutionary product simplifying and streamlining the process of maintaining and securing industrial operational networks.
Zero-Trust Security Level Model
No device on your network can communicate to another without your explicit permission. You create device to device communication rules that OT Network Controller propagates to the switches and centrally manages.

All Information about your network in one place
Continuously up to date network information about devices, switches, bandwidth usage. Unknown traffic blocked and flagged for you.
Self-Healing Network
Because OT Network Controller centrally manages the network and traffic by device and not by switch, moving a device from one port or one switch to another is automatically handled. If there is a break in the network wire, communication is automatically re-routed and you are notified. No more dead communications because of a cable being plugged into the wrong port.


Authorized Communication
DYNICS' approach to traffic engineering allows complexity at scale while allowing fine-grained control. The user can manage traffic at a high level – e.g. what zone to zone communications are permitted – or via very granular rules such as “a specific PLC is allowed to communicate with a specific HMI over DNP-3.”
Visual Network Management
OT Network Controller is designed by OT network experts for OT network users. You don’t think of your plant in terms of VLANs and subnets. You care that this PLC can get data to that HMI. Manage your network the way you think.
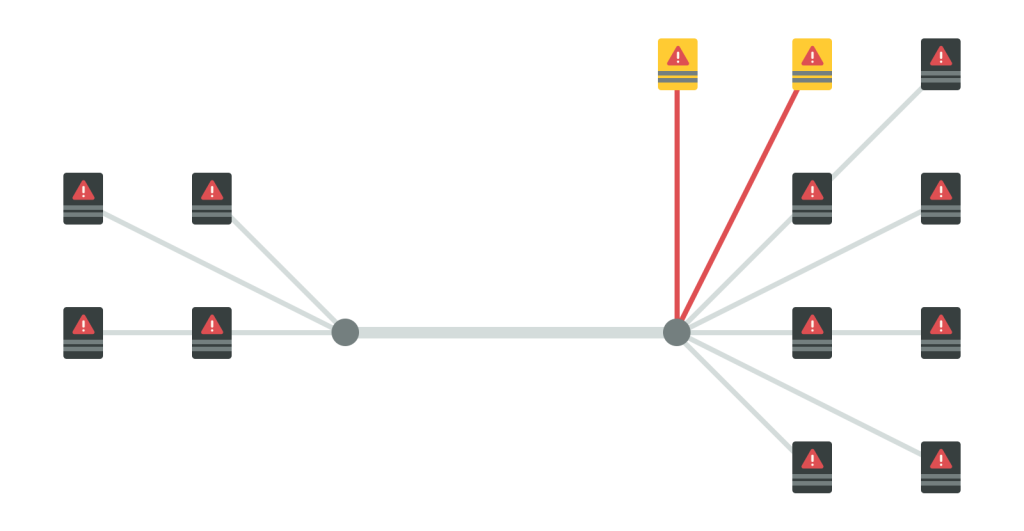
Security Zone Management
DYNICS provides an innovative approach to network segmentation via the creation of security zones through simple drag and drop.
Switches
No more need to buy expensive managed switches. With OT Network Controller managing switches, simply buy an SDN enabled switch from your favorite vendor.
Speed
Operations that used to require reconfiguring a switch now are handled automatically. Changes required in the network are now simple to implement.
System Policy Management
In addition to simplified traffic engineering via zones and device types, DYNICS provides dynamic, API-based control by allowing configuration change sets to be grouped as policies. These policies can be enabled or disabled at any time, vastly simplifying operational workflows. The system will support both a default policy of denying that access alongside an operational policy of allowing that access, and switching between them can be done via a remote process driven by a change management workflow or via a few clicks in the user interface.

Feature-Rich Performance
Designed for Security and Scale
Gain peace of mind with enterprise-grade solutions tailor-made to secure and scale DYNICS across your entire organization.

Want to learn more? Download Veracity's white paper
Security
Switches will not pass any communication without first assuring with OT Network Controller that it is allowed. No more open ports for bad actors to access. Lock down even the oldest PLCs and other devices without expensive upgrades.
Automation
North bound API allows programmatic integration with business and other security applications.
Reliability
Central network management allows for any network topology. Even supports a mesh network of switches for the ultimate speed and resilience.
Frequently Asked Questions
SDN or Software Defined Networking is an open standard that allows the programmatic management of network traffic. It is very commonly used in cloud applications and distributed networking by the major players in those industries.
Deny by Default means that no network communication traffic is allowed through switches unless explicitly defined as acceptable by the system.
A Zero Trust Network Architecture requires that no device on the network can be trusted by default. Typical networks will allow network communication if you are within the same subnet. OT Network Controller will not allow any network communication traffic that is not explicitly authorized by the system no matter where you plug in the device.
Net-Optix requires a Linux computer that runs as the network controller and network switches that support SDN. We recommend Dynics and SEL switches, but many others support SDN.
We recommend having one of our authorized integration partners install OT Network Controller for you. Please see our partners page to find the best one for you.
How do you think about your plant floor operations? Most people do not think of it in terms of network segregation. Most people think of wanting this PLC to communicate with that HMI. This is how OT Network Controller presents your network to you. This allows the people who maintain the operations to also manage the network.
Yes you can. With learn mode, the system can watch existing network traffic to create the rules required within the system getting you up and running very quickly. OT Network Controller does require SDN switches and if your current system does not support, SDN, we will work with you on the best and most cost effective implementation.
Like most security solutions, OT Network Controller is a software-as-a-service subscription solution. Pricing is based on the size of your network and which options a required for your unique installation. Please contact us for more information.
“The reason we picked OT Network Controller is because it has allowed our team to offer a differentiated networking solution to our customers that simplifies their OT network while providing a highly secure environment. “

